Deploying any next-generation firewall (NGFW) in a public cloud environment is challenging, not just because of the firewall itself but also because of the public cloud networking services practitioners must use. The job of understanding cloud networking complexities to ensure a successfully configured and maintained firewall deployment is no small task. It’s a task that is possible — though difficult — and it comes with performance, scale, and visibility tradeoffs that must be considered closely. This blog explores Aviatrix’s intelligent orchestration and control service to simplify the deployment of Palo Alto Networks VM-Series Firewalls and eliminate those tradeoffs.
Aviatrix Firewall Network Service
Aviatrix’s Firewall Network (aka FireNet) framework is part of its Secure Cloud Network platform. The Firewall Network provides a policy-based framework allowing 3rd party appliances/services to be inserted in the traffic flow by combining both the intelligent controller and transit gateway services. The service enables the simple insertion of Next-Generation Firewalls (NGFW) or other 3rd party appliances (such as F5) into AWS and other CSP (Cloud Service Provider) environments without sacrificing performance, scale, or visibility. The Aviatrix intelligent controller handles orchestration, visibility, health-check, alerts, and dynamic updates for all routing elements. The Aviatrix transit gateway service offers cost-optimized, active/active, and dynamic load balancing across multiple firewalls with high-performance encrypted links.
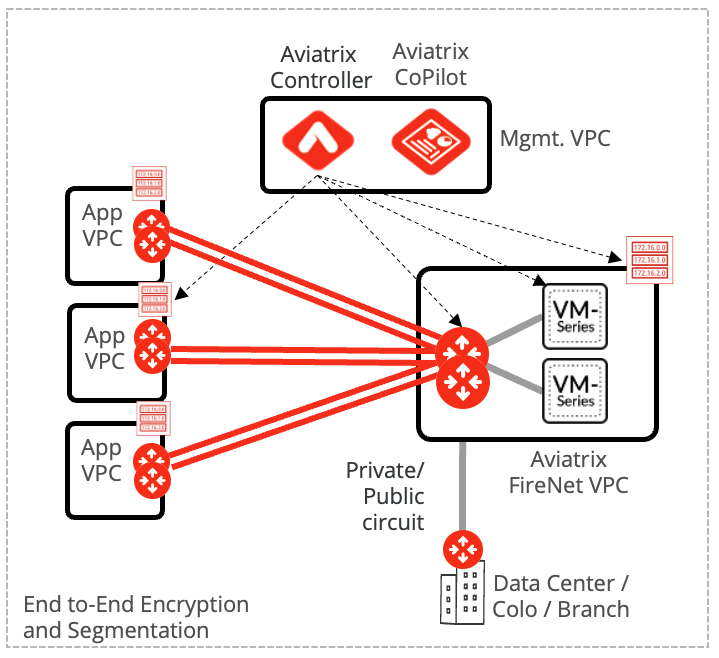
The Aviatrix Firewall Network Service leverages the combination of its intelligent orchestration and control as well as policy-based routing services to remove CSP networking complexities such as lack of route propagation, IPSec tunnels, and BGP; or use of source address translation (SNAT). Eliminating these constraints allows Palo Alto VM-Series firewalls to operate at optimal performance and at native throughput with encryption. Removing the need to use SNAT allows session stickiness and source address to be retained for full visibility. The firewall network service is deployed in multiple availability zones for active redundancy and scale-out load balancing. With Aviatrix, Palo Alto Networks VM-Series can achieve optimal performance, scale, and visibility.
Key benefits of bringing the Palo Alto Networks VM-Series to Aviatrix Transit Gateway environments include:
- Seamless and effortless integration of NGFW for deep packet inspection
- Automate end-to-end route propagation with Aviatrix intelligent orchestration and control service
- Unlock the full potential for NGFW by eliminating the IPSec and SNAT bottlenecks
- Achieve line-rate throughput with active/active, end-to-end encryption with cost-optimized design
- Enable scale-out and scale-up redundancy with ease
- Perform in-line traffic inspection based on user-defined policies for all traffic flows such as E/W, N/S, Egress, and Ingress
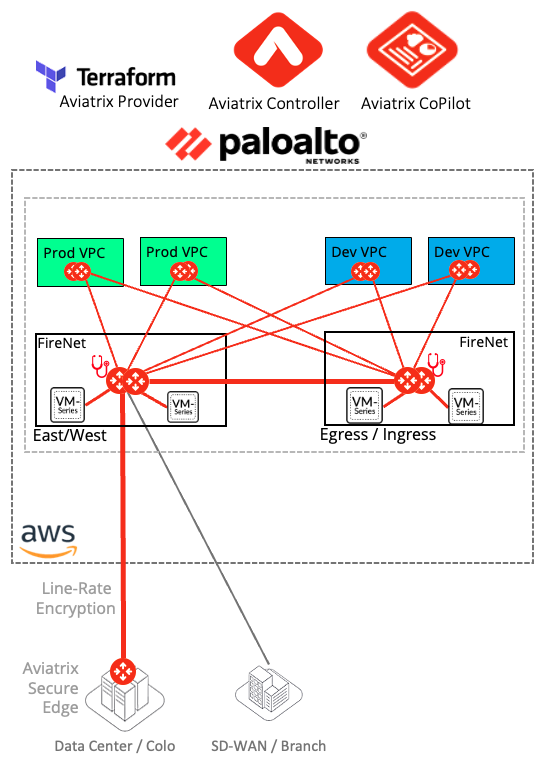
Business and Technical Advantages of using Aviatrix for NGFW Design/Deploy
Let’s discover how Aviatrix helps secure your missing critical applications using Next Generation Firewalls.
Increase ROI by getting the best performance out of your NGFW
Getting the optimal performance out of your NGFW in the cloud is about efficiently redirecting packets to the NGFW. One of the most common ways of doing this is to create IPSec tunnels between VPCs and the firewall instances. IPSec is an excellent technology for encrypting traffic, but it has performance limitations. An IPSec tunnel between the NGFW and AWS VPN Gateway (VGW) reduces the bandwidth of the traffic going in and out of the NGFW. No matter how much throughput the NGFW can handle, IPSec will limit how much traffic a single instance of the firewall can process. This is like having a wide garden hose that’s clamped somewhere in the middle. In order to reach the highest level of optimization, you want every bit of your NGFW’s compute power to be spent on what it is meant to do.
Aviatrix FireNet eliminates the need for IPSec and frees the NGFW from having to deal with any of the IPSec overhead. Aviatrix steers the traffic to NGFW instances in the FireNet VPC without building IPSec tunnels all the way to NGFW. This steering method offers a very high throughput (~90 Gbps) and does not introduce a performance bottleneck into your application’s design. This is a huge improvement over VPN tunnels connecting to VGW that cap at 1.25 Gbps. As such, it significantly improves the technical and economic efficiency of the entire architecture.
Reduce cost, and enhance visibility with policy-based zero-trust protection
In order to secure your workload with NGFW using the resources and services provided by CSP, you will have to rely on VPN tunnels or Geneve/VXLAN overlay to pipe traffic to and from the NGFW. This approach reduces the visibility because these native tools become the black boxes to various stakeholders and operations teams. The lack of visibility could cause serious issues and increases MTTR.
We have also noticed that some designs propose deploying NGFW in every application/workload VPC. This approach increases the overall cost of the deployment and creates a management and operations nightmare for the Day2 Ops teams. Aviatrix reference architecture recommends a cost-effective design that allows NGFW to be deployed in a centralized FireNet VPC.
Native or NGFW vendor designs usually do not offer a policy-based model to steer the traffic. They follow an all or none type approach where each and every VPC is inspected by the NGFW. Aviatrix provides NGFW vendor integration with a very simple policy model which allows enterprises to select the App or Workload they require for inspection by the NGFW.
Increase agility with out-of-box automation and self-healing capabilities
Aviatrix FireNet enables inspection of cloud traffic through a cluster of NGFWs while maintaining native functionality and visibility. The Aviatrix controller handles orchestration and ongoing management, monitoring, and health-check of firewalls as well as critical elements of cloud networking so that you don’t have to work around the limitations imposed by the cloud network controls. Aviatrix requires no manual modification of route tables, as the controller handles end-to-end route propagation with dynamic routing in place.
Scale without loss of visibility
As is the rule in the computing world, when you scale out, you need to ensure that the state is maintained properly across the scaled systems and traffic is distributed accurately. Another major part of FireNet architecture is using Aviatrix gateways to load balancing across firewalls. If you have considered using AWS Transit Gateway and its Equal Cost MultiPathing (ECMP) capability, you may know that in order to avoid asymmetric routing, you need to perform SNAT at the firewall. This will replace the original source of the traffic with the firewall’s IP, which could become problematic for any application that requires visibility into the traffic’s source address.
For example, if you have an application tracking transactions based on the traffic’s source, the traffic’s source will always be the firewall’s interface instead of the actual source. This diminishes the flexibility and applicability of this architecture for East-West inspection. With Aviatrix, you do not need to make this tradeoff between visibility and scalability. With Aviatrix Transit Gateway, the FireNet framework manages load balancing across the firewall instances and retains visibility across all traffic.
Increased time to market with Aviatrix
Aviatrix helps speed up build and manage your complex AWS environment beyond firewall insertion. Enterprises have set high expectations for infrastructure speed, security and agility in a cloud-based world. The Aviatrix Secure Cloud Network Platform embeds security right into the data-palne. It further enhances the application security postures by seamlessly inserting and chaining 3rd party NGFW with a policy-based FireNet framework. The platform leverages intelligent orchestration and control with the Aviatrix repeatable and cloud agnostic architecture, in concert with native public cloud services to significantly increase agility in response to business demands. Gone are the days of asking users to wait for weeks to get what they need in the cloud. With Aviatrix, you can react and service your business and customers much faster.

