By Tim McConnaughy and Abdul Rahim
You may have seen Aviatrix’s name come up in connection with the recent launch of the AWS Cloud WAN Service Insertion feature to simplify connectivity and inspection architectures. As an industry-leading cloud networking and security solution and an AWS Partner, Aviatrix integrates with AWS Cloud WAN to unlock advanced networking and security capabilities and simplify connectivity across and between clouds, enabling customers to fully leverage the power of AWS. Using this new Service Insertion integration, customers can now achieve centralized east-west and internet-egress inspection, secure multicloud connectivity, encrypted on-premises connectivity, secure connectivity to AWS partitions such as AWS China and AWS GovCloud, and provides B2B connectivity with partners.
What exactly does this mean for your cloud, networking, and security teams and your businesses? Let’s dive deeper on the integration, use cases, and benefits for integrating AWS Cloud WAN Service Insertion with Aviatrix.
Aviatrix Integration with AWS Cloud WAN Service Insertion: An Overview
Aviatrix integrates with the AWS Cloud WAN Service Insertion feature by deploying Aviatrix Gateways inside an AWS VPC. Aviatrix supports AWS Cloud WAN VPC, VPN, and Connect attachment to participate in the AWS Cloud WAN Network Function Group. AWS Cloud WAN policy document controls route propagation to the Cloud WAN workload segment and network function group route tables.
Customers use send-to segment-action for north-south and internet egress traffic inspection. Customers can additionally leverage send-via segment-action for east-west traffic inspection. Aviatrix supports all service insertion segment-actions, segment insertion modes, and edge-overrides settings.
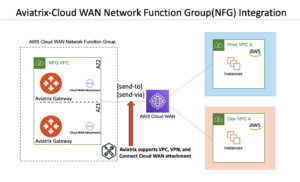
Figure 1: Aviatrix Integration with AWS Cloud WAN Service Insertion
Following are the two deployment models supported with AWS Cloud WAN Service Insertion:
Aviatrix Distributed Cloud Firewall (DCF)
Aviatrix’s innovative Distributed Cloud Firewall (DCF) allows customers to centralize the creation of security policy while distributing its enforcement. Some of the major benefits of using Aviatrix DCF with AWS Cloud WAN Service Insertion include:
Centralized Security Management: By decentralizing security enforcement while centralizing policy management, Aviatrix DCF simplifies security across your entire cloud infrastructure – including multiple cloud service providers (CSPs) or CSP regions. It uses cloud-aware criteria and objects to create a SmartGroup, which can span any number of workloads and VPCs dynamically, then create a single security policy to enforce across all of them.
Unified Security Policy: Rather than worry about all the different security enforcement options and how to configure them in every cloud, DCF supports cloud-aware metadata tagging with SmartGroups that let you create a policy once for east-west and internet egress traffic flows and let Aviatrix determine how to properly enforce it in each cloud based on the intent.
Industry-Leading Firewall and Threat Detection: Aviatrix leverages Suricata for threat detection and eBPF for firewall enforcement, matching the capability of any L4 firewall on the market at a fraction of the price.
Domain Security with WebGroups: Choose what domains to allow or block based on policy.
TLS Decryption: Securely inspect encrypted web traffic for greater workload visibility.
Deep network traffic visibility and diagnostics.
This integration supports the AWS Cloud WAN VPC attachment (as shown in figure 2) and is available to customers in early-access mode.
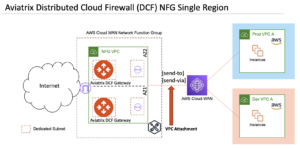
Figure 2: Aviatrix Distributed Cloud Firewall (DCF) Integration with AWS Cloud WAN Service Insertion
Aviatrix Transit FireNet
The Aviatrix Transit FireNet solution enables the seamless deployment and insertion of next-generation firewalls (NGFWs) into AWS and other CSP environments without sacrificing performance, scale, or traffic visibility. The Aviatrix Transit Gateway offers cost-optimized, active/active, and dynamic load balancing across multiple firewalls.
Aviatrix handles orchestration, visibility, health-check, alerts, and dynamic updates for all routing elements. It offers optional deployment and integration with AWS Gateway Load Balancer. Aviatrix Transit FireNet uses AWS Cloud WAN Connect or VPN attachment for NFG association. Key features of using Aviatrix Transit FireNet with AWS Cloud WAN Service Insertion include:
Deployment and integration of NGFW with or without AWS GWLB.
Deep network traffic visibility and diagnostics.
Traffic inspection based on user-defined policies for all traffic flows such as east-west (within or between Cloud WAN segments), north-south (on-premises), B2B connections, multicloud, AWS Gov Cloud, AWS China, Internet egress, and Internet ingress.
Support for exclusion lists to bypass east-west traffic inspection for specified CIDRs.
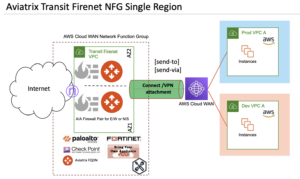
Figure 3: Aviatrix Transit FireNet Integration with AWS Cloud WAN Service Insertion
Aviatrix Integration in the Real World
Now let’s look at some of the advanced use cases that can be achieved by integrating Aviatrix with AWS Cloud WAN Service Insertion.
Centralized Internet Egress Inspection
The Aviatrix DCF or Aviatrix Transit FireNet Solution can be used for a Centralized Internet Egress use case. send-to segment-action within AWS Cloud WAN Policy is required to insert default route (0/0) into the associated Cloud WAN segments’ route tables.
Aviatrix DCF Gateway combines both NAT and security enforcement functionality. It supports, L4 and L7 policies, FQDN and URL based filtering, IDS, and TLS decryption.
In Figure 4, we show two Aviatrix DCF Gateways in a single VPC. The VPC is attached to the AWS Cloud WAN (appliance mode is optional for this use case). Appropriate tags should be assigned while creating the Cloud WAN VPC attachment to associate the VPC to the appropriate NFG. Additionally, Aviatrix DCF Gateways can be scaled vertically and/or horizontally.
The same deployment can be extended across multiple VPCs within or across AWS regions. Multiple NFGs within a single region can be deployed to implement dedicated internet egress control for each Cloud WAN segment.
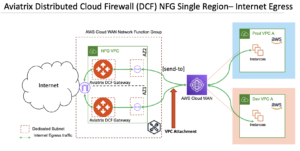
Figure 4: Aviatrix Distributed Cloud Firewall (DCF) in Centralized Internet Egress Design
Figure 5 demonstrates the Aviatrix Transit FireNet Solution with either Aviatrix Egress FQDN Gateways or using a Firewall vendor of your choice for centralized internet egress deployment. Aviatrix Transit Gateways advertise a default route (0/0) over BGP to AWS Cloud WAN using Connect or VPN attachment. AWS Cloud WAN advertises all the workload segment VPC CIDRs to Aviatrix Transit Gateways to ensure that Aviatrix Transit Gateways have a return traffic path. Aviatrix Transit Gateways perform 5-tuple (default) or 2-tuple (configurable) hashing to forward traffic to the healthy firewalls. Aviatrix can optionally orchestrate and manage AWS Gateway load balancer and Gateway load balancer endpoints.
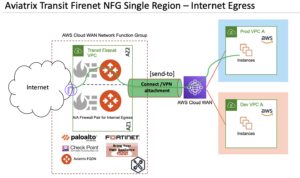
Figure 5: Aviatrix Transit FireNet in Centralized Internet Egress
Centralized East-West Inspection
Aviatrix DCF or Aviatrix Transit FireNet can be used for centralized east-west traffic inspection. send-via segment-action within AWS Cloud WAN policy is required for this use-case. It ensures symmetric traffic forwarding to an NFG.
Aviatrix DCF supports L4 and L7 policies for east-west traffic patterns. The NFG VPC attachment to AWS Cloud WAN will require appliance mode (as shown in Figure 6).
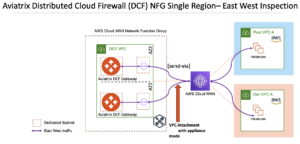
Figure 6: Aviatrix DCF in Centralized East-West Inspection
With Aviatrix Transit FireNet, AWS Cloud WAN advertises all the workload segment VPC CIDRs to Aviatrix Transit Gateways with Connect or VPN attachment to facilitate return traffic. Aviatrix Transit Gateways performs 5-tuple (default) or 2-tuple (configurable) hashing to forward traffic to the healthy firewalls.
Aviatrix Transit Gateways can optionally bypass east-west inspection for specified CIDRs. This feature is useful to exclude some applications within a VPC from NGFW inspection.
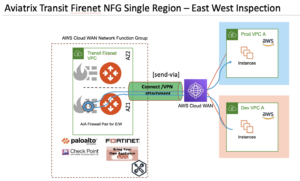
Figure 7: Aviatrix Transit FireNet in Centralized East-West Inspection
Encrypted Connectivity Across Clouds
AWS Cloud WAN can integrate with Aviatrix Transit to easily extend connectivity to workloads and services hosted in any cloud provider. Aviatrix Transit Gateways interconnect between clouds using patented high performance encryption (HPE). The HPE can be established over the public internet or a dedicated private underlay. Meanwhile, all traffic transiting through the Aviatrix data plane benefits from deep visibility with Aviatrix CoPilot.
This integration requires send-to segment-action to send traffic to Aviatrix Transit (NFG) going to other cloud. AWS Cloud WAN rejects any prefixes except 0/0 when advertised via Connect attachment associated with an NFG. Customers can implement BGP traffic engineering features baked into the Aviatrix solution to maintain traffic symmetry.
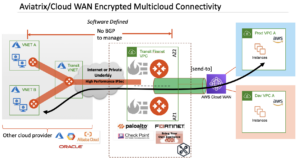
Figure 8: Aviatrix Transit FireNet for Encrypted Multicloud connectivity
Encrypted On-premises Connectivity
Aviatrix encrypts dataflows by default. The strong security and encryption model for Aviatrix Transit in the cloud can be extend to on-premises connectivity using Aviatrix Secure Edge. This ensures all traffic from on-premises to the cloud is encrypted end-to-end, even as it travels through intermediary networking devices, where MACsec alone offers protection between only the Direct Connect endpoints.
Customers can use AWS Direct Connect hosted (even sub-1 Gbps) or dedicated connections using Hosted/Private VIFs to provide an underlay for the HPE connection between Aviatrix Secure Edge on-prem and your Aviatrix Transit in the cloud (as shown in Figure 9).
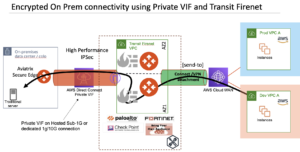
Figure 9: Encrypted on-premises connectivity using Private VIF and Transit FireNet
Multi-Region Architecture
Figure 10 elaborates a multi-region deployment with Aviatrix and AWS Cloud WAN. As shown, customers can use Aviatrix DCF and Aviatrix Transit FireNet in the same deployment.
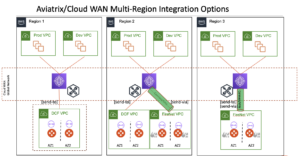
Additionally, the following uses cases can also be solved by integrating Aviatrix Transit with AWS Cloud WAN.
Connectivity to Partners remote networks
Connectivity between AWS partitions including AWS Gov Cloud and AWS China
Connectivity to SASE Solution
Connectivity to SD-WAN Solution using BGP over LAN (without GRE or IPSec support required from SDWAN platform)
Connectivity to AWS Regions where AWS Cloud WAN has not yet launched
Available Deployment Options
Understanding the integration and different use cases we can achieve by using Aviatrix with AWS Cloud WAN Service Insertion, perhaps you’re ready to get started. The table below provides a summary of the deployment options available to customers.
Aviatrix’s innovative Distributed Cloud Firewall allows customers to centralize the creation of security policy while distributing its enforcement. Leverages Smart Groups to build policies using CSP tags. Same Unified policy works across AWS regions and/or other clouds.
Internet Egress
East-West (within or between Cloud WAN segments)
VPC Aviatrix Transit FireNet Solution
Aviatrix Transit FireNet solution enables the seamless deployment and insertion of next-generation firewalls (NGFW). It allows customers to use the vendor of their choice and extends secure connectivity from AWS to on-premises and/or other public clouds.
Internet Egress
East-West (within or between Cloud WAN segments)
North-South (on-premises)
Multicloud connectivity
AWS Gov Cloud Connectivity
AWS China Connectivity
B2B Connectivity
Connect, VPN
AWS & Aviatrix: Better Together
Our integration with AWS Cloud WAN highlights the deep relationship that Aviatrix has with AWS, and our commitment to providing advanced capabilities and interoperability to AWS customers. Whether you are using AWS alone or as part of a larger cloud strategy, Aviatrix provides the cloud networking and security capabilities required by today’s enterprises.
Experience the ease of cloud networking with Aviatrix. To get started, please register for Aviatrix 101 session for an introduction to Aviatrix. You can also register for our next Secure Cloud Networking Immersion Day with AWS for a hands-on opportunity with AWS and Aviatrix together, or schedule a demo.
About the Authors

Abdul Rahim is a Principal Solutions Architect at Aviatrix. He is a triple CCIE with over 25 years of experience in networking field working with AWS, VMware, and Cisco. He has a bachelor’s in electrical engineering and MS in Telecommunications. He is passionate about improving customers cloud networking experience.

Tim McConnaughy is a Technical Marketing Engineer with Aviatrix. He has been in the industry over 15 years and has written various books about networking and co-hosts a cloud networking podcast called Cables2Clouds.


















