

Future-Proof Your Cloud Strategy
Get the secure networking foundation that gives you back power, control, security, and consistent tools.
We help our customers solve business challenges:
0 %
average savings for egress
Use our TCO calculator to estimate cloud security savings with Aviatrix versus cloud provider solutions.
Improve cloud security
Consistently apply the same security policies, controls, and architectures across any cloud to reduce risk of gaps and inconsistencies, simplify audits, and stay compliant.


Simplify management
Use a single interface to view, monitor, and manage multiple cloud networks. Streamline operations with consolidated control.

Contain cloud costs
Process your cloud traffic more efficiently with flat hourly billing and no added cost for throughput. Selectively block egress traffic and cap monthly costs.

Take advantage of AIs
Leverage the automation and performance advantages of AI in managing your cloud. Tap into AI-enabled UX and easy to use natural language querying to find issues fast.

Industry-Leading Cloud Network Security Solutions
Optimize your cloud network security from egress traffic to the datacenter edge, all without re-architecting your existing network – and you can deploy in minutes.
- Aviatrix Cloud Firewall™
Enforce Zero Trust. Lower Cloud Costs.
Overcome the limitations of native cloud provider security options with Aviatrix. Protect all of your data while improving network performance and operational costs.
Achieve Zero Trust control of your cloud perimeter with URL filtering, geo-blocking, geolocation-based monitoring, advanced threat detection, and network segmentation.
Gain insight into traffic patterns, anomaly detection, and cost analysis. Then take fast action.
Support Kubernetes, Docker, and Pods and reduce the challenges created by microservices such as IP exhaustion and governance and security.
Count on flat-rate billing with no additional throughput costs. Get clear insight into your billing.

- Secure Datacenter Edge
High-Speed, Encrypted Connectivity for Hybrid IT
Deliver hybrid cloud connectivity without compromise.
Encrypted, line-rate performance with single-region, multi-region, or multicloud redundancy, visibility, and troubleshooting.
Ensure secure, compliant connections across multiple cloud environments.
Simplify operations with real-time visibility and automated workflows.
Optimize performance without sacrificing security with Megaport.


500+ Enterprises Trust Aviatrix
Including 10% of the Fortune 500



















Aviatrix Cloud Network Security Platform
Consolidate networking, management, automation, and security into one enterprise-grade solution.
As the only network security solution built specifically for the cloud, the Aviatrix Platform provides distributed perimeter security with centralized control, visibility, and management.
Available as a self-service Enterprise solution or a fully managed Platform-as-a-Service, Aviatrix makes cloud orchestration, security, and reliability effortless.
Providing secure, high-speed multi-cluster networking for dynamic workloads to resolve IP exhaustion, de-risk single or multi-cluster egress, and unify security policies across clusters.
Application Modernization
Modernize application and security with secure, high-performance networking solutions, offering advanced connectivity, automation, and robust security for scalable, cloud-native environments like Kubernetes.
Zero Trust
Aviatrix embeds zero trust into the cloud network, securing workloads and connections with identity-based policies. It prevents lateral movement, blocks unauthorized access, and stops data exfiltration.
Gen AI
Integrated GenAI gives users enriched context for workload discovery, such as flagging application misconfiguration or potential threats, security policy recommendations, and accelerated troubleshooting.

Empowering Enterprises Worldwide with Modern Cloud Network Security
We’re proud to support more than 500 innovative organizations across a range of industries, including:
- Healthcare
- Manufacturing
- Financial Services
- Retail
- Software
Healthcare Transformed with Aviatrix Cloud Network Security Solutions
Secure patient data, streamline telehealth services, and support compliance with cloud network security honed for the critical needs of the healthcare industry.

The People Behind Cloud Success
We love hearing how cloud networking professionals use Aviatrix to make a difference.
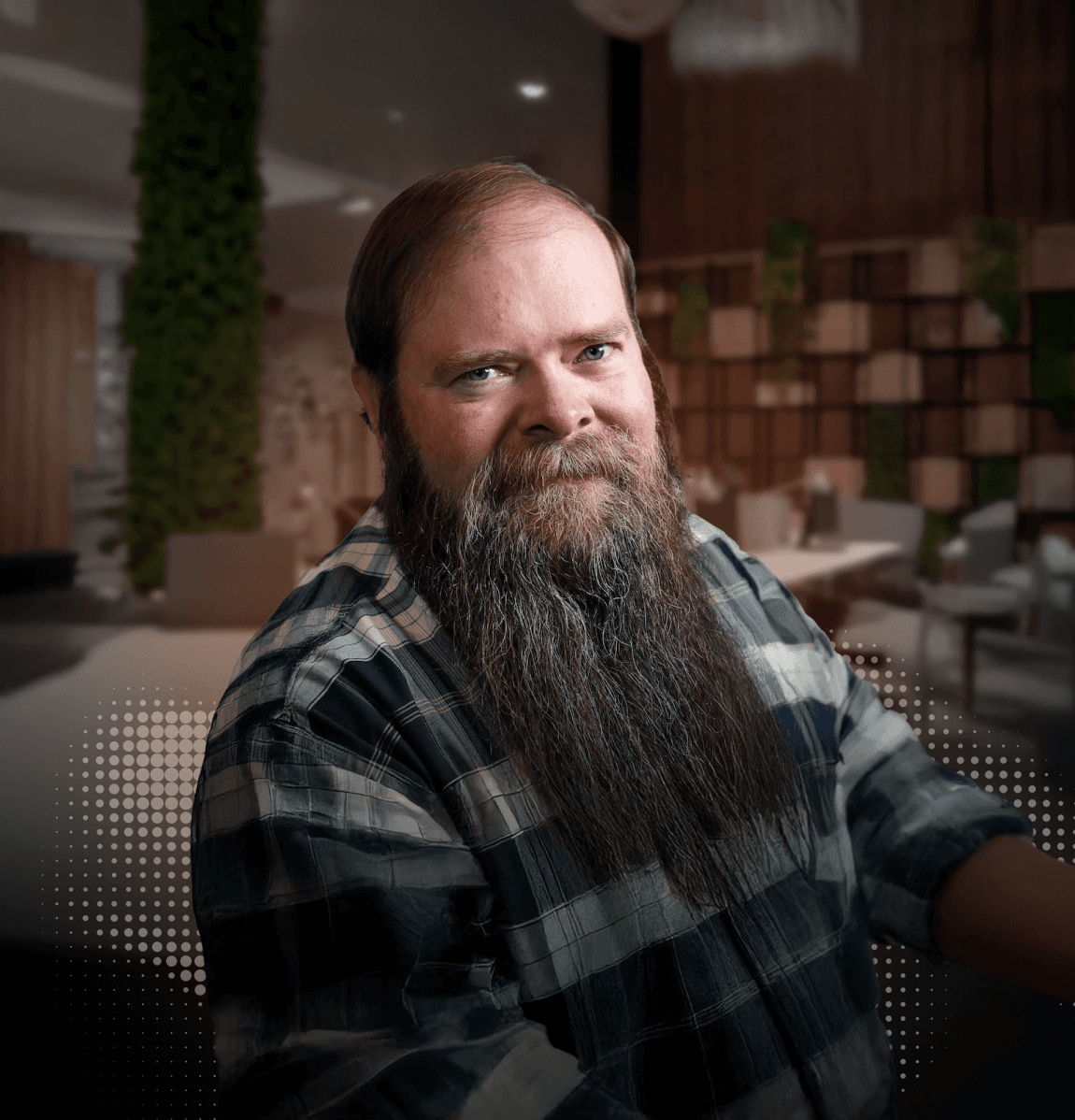
Toby Foss
The future of cloud networking is about embracing the ever-evolving landscape. Companies today must adapt or be left in the dust. I am proud of the automation that not only protects our global operations but also empowers my team to innovate and scale.

Cristian Critelli
Over the next decade, cloud networking will be transformed by AI-driven automation and predictive analytics – redefining resilience and drastically reducing downtime. The shift toward multi-region and multi-availability zone architectures will accelerate, ensuring seamless continuity and empowering enterprises to build fault-tolerant infrastructures across distributed cloud environments.

Roy Long
I thrive on helping organizations navigate the complexities of cloud technology by building flexible, scalable, secure solutions. The future of cloud networking is not about mastering just one tool—it’s about fostering continuous adaptability and resilience. The ability to stay agile in the face of evolving challenges is what drives success in the cloud landscape.

Mark Noorman
I love those 'aha' moments when colleagues or customers realize they need to think differently to tackle network challenges. Many assume cloud networking has to follow a rigid structure, but platforms like Aviatrix show it can be much simpler. It’s about sharing knowledge, drawing from experience, and helping others design smarter, more effective solutions.
See How Leading Companies Succeed with Aviatrix
We serve leading enterprises in solving cloud network security challenges.
Industry-Leading Experience. World-Class Partners.
Our trusted network of partners and integrations enables faster, more reliable deployments, powers more agile operations, and enhances our customers' overall cloud experience.



Discover How Cloud Network Security Is Advancing.
We’re Here To Help You Find Your Path to Improved Cloud Network Security.
Let’s put industry-leading cloud network security to work for you.
























