How do I implement a stateful firewall for network traffic across VPCs?
AWS offers two AWS-native ways to implement security policies across VPCs: Network ACLs and Security groups. Both of these have limitations that can get in the way of cloud adoption. We will not cover these limitations in detail here. But, on a high level:
- ACLs are not stateful which makes it extremely challenging in mid-to-large-scale environments.
- Security Groups are tied to individual hosts and have a limit of 50 rules. Because of these limitations, AWS customers commonly use security groups to firewall within a VPC.
Cross VPC firewalling has become an important consideration in recent years as the number of VPCs have grown to the 100s for a typical AWS customer. Some customers have implemented commercially available firewalls in each VPC. This will serve the purpose, but at a much higher cost. If you are trying to implement a stateful firewall for cross VPC traffic and log the traffic (stats/allows/denies) there is an easier and more cost effective solution to consider – use Aviatrix gateways.
Aviatrix gateways have a stateful firewall built into the software. This firewall feature is normally used with Encrypted peering or FQDN filtering, but can also be used by itself.
The following diagram shows how you can implement this solution:
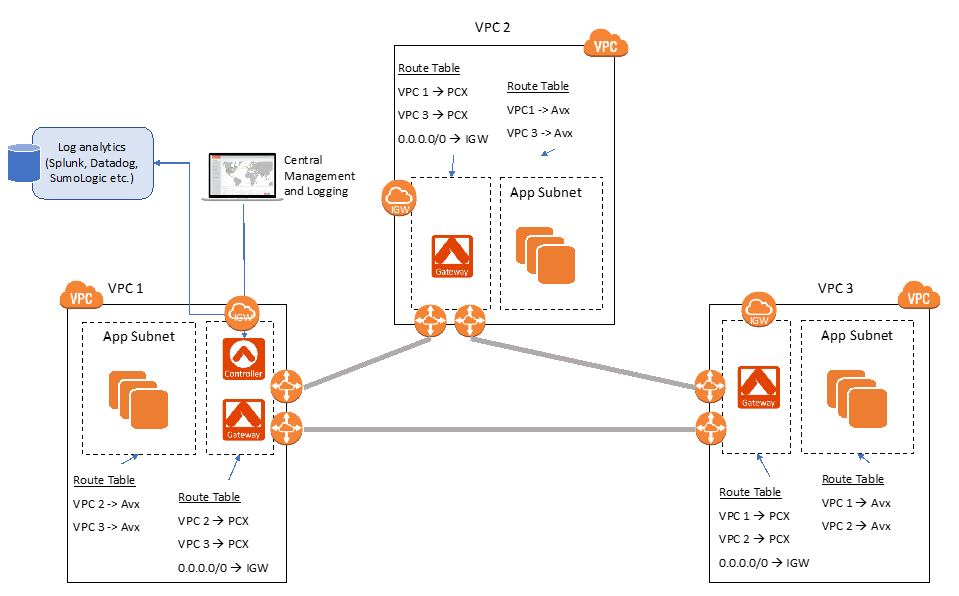
The basic idea is to set up VPC peering and then filter traffic leaving (egress) or entering (ingress) via the peering connections. To do this:
- Peer the VPCs that need filtering using AWS peering.
- Choose (or create) a subnet that has IGW access in each VPC and create an Aviatrix Gateway in these subnets (through the Aviatrix Controller or using the APIs).
- These subnets with Aviatrix Gateways have these entries in their route table:
- Point 0.0.0.0/0 to IGW
- Point other VPC CIDRs to the respective AWS peering connections (pcx).
- All other subnets have their route table pointing to the Aviatrix Gateway for inter-VPC communication.
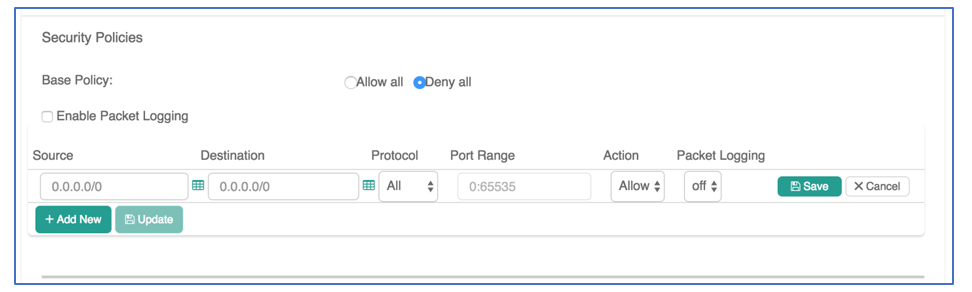
- Log into the Aviatrix Controller to create firewall policies:
- Go to the security tab: Security -> Stateful Firewall -> Policy tab
- Select each gateway from the list -> Click Edit on the top of the list
- Use the Security Policy UI to Allow or Deny traffic based on Source, Destination, Protocol and Port Range.
Additional Features:
- You can also log traffic to Log Analytics tools like Splunk, DataDog, SumoLogic etc. for audit and compliance purposes.
- Enable Logging (under Settings) to your log tool of choice.
- Select “Enable Packet Logging” in the Security Policy UI (screenshot above).
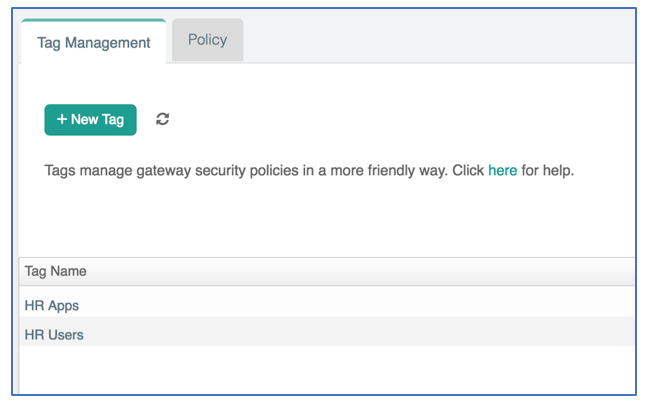
- You can also group IP addresses and tag them with human-readable names. This makes it easier to manage and apply firewall policies. Tagging can be accomplished under the Tag Management tab in the Security view.
Become the cloud networking hero of your business.
See how Aviatrix can increase security and resiliency while minimizing cost, skills gap, and deployment time.
