Ingress vs. Egress in the Cloud
The concepts of Egress and Ingress in cloud security are pivotal for managing network traffic. While these terms are broadly used to describe entering and exiting in various contexts, their specific application in cloud networking is both distinct and critical for data security and network management.
Defining Egress vs. Ingress
What is Egress?
Egress refers to the flow of data moving out of a private network into the public internet or another external network. This process is integral to network operations, especially in cloud environments where controlled data movement is paramount for security and efficiency.
What is Ingress?
Ingress, conversely, pertains to the flow of data into a private network from an external source, typically the public internet. In cloud computing, managing ingress effectively is key to maintaining network integrity and security.
Ingress & Egress in the Cloud
Egress in Cloud Networks
In cloud-based systems, egress traffic involves data transmission from a controlled, internal network space—such as a data center or cloud infrastructure—to the wider internet. This movement requires careful handling, particularly through Network Address Translation (NAT), to ensure secure and authorized data egress. The role of firewalls is also critical in monitoring and allowing this outbound traffic, particularly in response to internal requests or established network sessions. See the picture below for reference.
Egress:
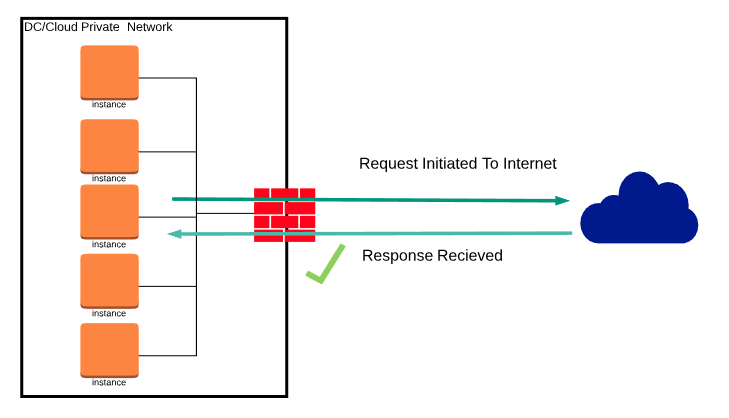
Ingress in Cloud Environments
In cloud environments, ingress involves unsolicited external traffic attempting to access the private network. This can include external data packets and requests that are not responses to internal actions. Firewalls are essential in these scenarios, configured to block or scrutinize incoming traffic unless specific security policies and configurations are in place to permit certain types of ingress. See the picture below for reference.
Ingress:
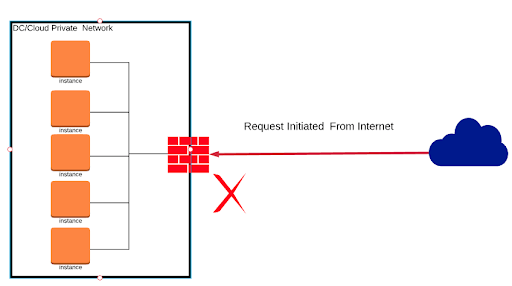
Become the cloud networking hero of your business.
See how Aviatrix can increase security and resiliency while minimizing cost, skills gap, and deployment time.
