Egress Control in Cloud Networking
Egress control is crucial in cloud networking, serving as the frontline defense against data exfiltration and unauthorized access to potentially harmful internet endpoints. By implementing stringent egress filtering measures, organizations can ensure that only trusted sites are accessible, significantly reducing the risk of interactions with malicious entities and preventing potential infections from communicating with external command-and-control locations.
What Is Egress Filtering?
Egress filtering governs the flow of data intended for external destinations, ensuring that it is scrutinized and permitted based on predefined security policies. This process is vital for preventing data from reaching dangerous hosts and for maintaining the integrity of cloud-based resources. Technologies such as egress-only internet gateways are instrumental in managing outbound communications, especially in IPv6 environments, by allowing outbound communication from virtual private clouds (VPCs) to the internet, while blocking unsolicited inbound traffic.
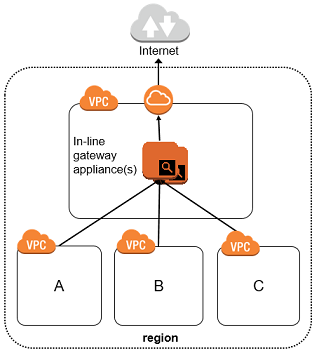
Strategies for Effective Egress Filtering
Deploying effective egress filtering involves several techniques, including anti-spoofing measures to prevent the flow of traffic with forged source addresses and internal service filters to block services prone to exploitation. Additionally, employing a “Deny-All” outbound policy ensures that only approved services can transmit data outside the network. Using proxies can further streamline traffic, reduce firewall load, and enhance security.
Deep-dive into Egress Security & Filtering
Egress filtering involves controlling any form of data bound to an external entity, passing through the edge router of the host network to reach its destination node. Several policies or filter rulesets have to be tested against before an outbound connection is allowed, otherwise, a dangerous host might be the target of a request from one of your machines. Egress-Only Internet Gateways are used to prevent the Internet from initiating an IPV6 connection with your instances by only allowing outbound communication over IPv6 from instances in your VPCs to the Internet.
Traffic from the instances in the subnet is forwarded by the egress-only Internet gateway to other AWS services or the Internet and a consequential response is sent back. An egress-only Internet gateway is created using the Amazon VPC console
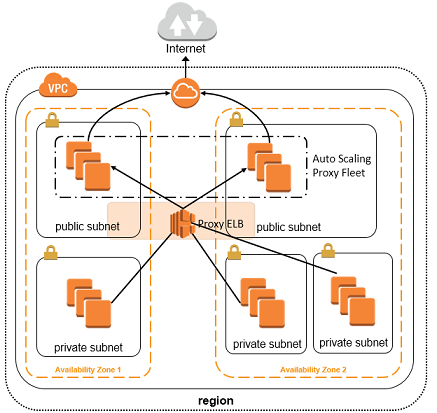
Several techniques can be used for egress filtering: deploying anti-spoofing filters that prevent the outbound flow of traffic with forged source addresses such as those from Distributed denial of service attacks. Certain services are usually reserved for internal networks and can be associated with exploitation, therefore, a filter for internal-only services is essential. Services often associated with malicious activities and those that should be restricted to a smaller number of known hosts should be filtered.
AWS VPCs provide NAT gateways but they have native AWS IP address limitations, and therefore egress traffic filtering can help mitigate data exfiltration from network assets. A Deny-All outbound policy, packet filters or firewall rule ensures nothing leaves the network without explicit permission, except those services identified in the egress traffic enforcement policy. The administrator can access the network and systems through granular restrictive rules. Limiting the addresses allowed to send data to the internet by configuring a policy that prevents IP spoofing which would allow the only source addresses from the IP network numbers assigned to pass the firewall in the internal network. Appropriate subnet masks should be applied to only pass traffic from address spaces that are used and block traffic from any private addresses from being forwarded over your internet circuit. Any network segments or VLANs that have no business establishing a network connection to internet servers should be blocked. Destination addresses that are listed in the DROP (Don’t route or peer) or BGP filter lists should not create any outbound connections. Web proxy performs URL and content filtering for HTTP to only allow outbound connections through the firewall from the proxies. For firewalls that negotiate and exchange PPP over Ethernet, blocking routing protocols at the firewall is essential.
Best Practices for Egress Filtering
Use a proxy whenever possible
By using proxy breakpoints in the network, your firewalls can only accept traffic from a few proxies and not the entire network. This limits the amount of traffic reaching the firewall and adds an extra layer of security to your outgoing traffic.
Use firewall configuration review tools
If the firewall is not configured for output filtering at the outset, its rule set is probably configured to allow unfiltered outbound access. However, since most firewalls have thousands or even tens of thousands of firewall rules, it is not practical to manually scan them to identify which ones are at risk. By using a firewall rule set parser against your firewall rule sets, you can immediately identify risks within the firewall, including rules allowing outbound at-risk traffic as well as open ports. Be sure to visualize these risks and evaluate the systems that use them.
Business justification for firewall outbound rules
Once all the outbound rules are locked in your firewall, create a policy that dictates that all future outbound rules are documented with business justification, why these rules were created, who uses them, which applications and which systems use them and who are the owners of the originating business process. This is not only useful for audits, but it is also useful to know what your firewall rules are for, especially when they allow packets to leave your network.
Review security zones
Your network likely has a DMZ, PCI zone, or other sensitive network segments that would not be directly accessible. These are key areas of your network, and firewalls for data entry and exit must be subject to even more scrutiny and control. Their firewalls must be treated with the same logging, reviewing, and managing procedures as your other firewalls interacting with external networks and are audited with regular frequency.
Leveraging Aviatrix for Advanced Egress Control
Aviatrix’s cloud networking solutions offer an advanced framework for egress control, providing enterprises with the tools needed to secure their cloud environments effectively. Through comprehensive policy management, real-time monitoring, and cutting-edge security features, Aviatrix empowers organizations to implement best-in-class egress filtering practices, ensuring secure, efficient, and compliant cloud operations.
Become the cloud networking hero of your business.
See how Aviatrix can increase security and resiliency while minimizing cost, skills gap, and deployment time.
