Aviatrix Validated Design
Multi-Cloud Network Architecture for Businesses with SaaS Offerings
Overview
Growth of Software as a Service (SaaS) companies has accelerated over the past decade as SaaS providers have enjoyed the agility and time-to-market advantages not possible with traditional Software as a Product (SaaP) delivery models. Multi-region and multi- cloud architectures are now enabling SaaS businesses to reach a growing number of customers around the globe.
However, as cloud centric delivery models become increasingly business critical, SaaS businesses discover that their customer’s and their own security and business requirements, service delivery quality objectives, and costs become more difficult to achieve.
The Aviatrix cloud network platform provides the proven solution SaaS providers need for enterprise-class cloud networking, security and operations required for incredibly complex SaaS environments. This document outlines the technical challenges and build verses buy decisions SaaS businesses face, the Aviatrix solution, and a provides a validated design that SaaS vendors require to streamline their cloud network and security infrastructure and overcome visibility and troubleshooting challenges.
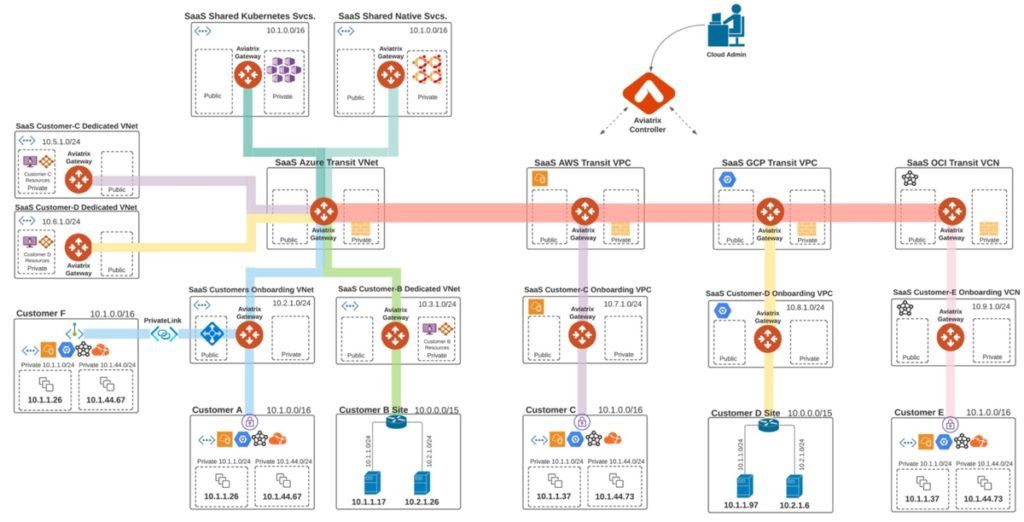
SaaS Vendor Challenges with Native Cloud Networking
The way enterprises consume SaaS services poses several challenges related to cloud networking and security, because native CSP constructs fall short of providing the enterprise-grade capabilities required to solve these challenges:
Secure onboarding of end-customers with overlapping IP space:
- End customers may have overlapping IPs with each other, as shown in the above diagram
- End customers may have overlapping IPs with the SaaS vendor’s applications address space. For example, Customer A using the same address space used by the SaaS provider for its own dedicated or shared resources
Often SaaS provider end-customers have business requirements or preferences that their data be hosted or processed in one cloud platform verses another. To meet customer requirements, SaaS providers must onboard these customers to the preferred cloud, forcing SaaS providers to maintain complex, inconsistent architectures unique to each cloud provider. To meet this challenge, a secure, high-performance multi-cloud network and security architecture is necessary to satisfy the end- customer requirement.
Security is a big challenge; SaaS providers are expected provide:
- Full segregation of the resources; end-customers must not be able to access each other’s dedicated resources
- Based on service agreements, end-customers should be able to securely access shared services
- Traffic from end-customers must be inspected by NextGen Firewalls before accessing shared services
Other challenges SaaS providers must overcome include:
- DIY (Do It Yourself) oriented SaaS providers with complex networking and security requirements face substantial Day 2 operational challenges when they go multi-cloud using this strategy due to architectural complexity and unmanageability. SaaS providers should not limit themselves to CSP provided native constructs
- SaaS providers find it infeasible to maintain separate operational teams for each unique cloud provider platform when customers require service delivery from a cloud other than the SaaS providers primary cloud.
- NextGen Firewall traffic inspection becomes a big challenge when end-customers are onboarded via Private Links
- SaaS provider architectures that restrict their customers from initiating sessions, only allowing unidirectional traffic flows
from cloud to customers - Native cloud provider tools lack the visibility and troubleshooting capabilities required for SaaS operations teams
Aviatrix Introduction – Multi-Cloud Network Architecture
Design Elements and Features
Aviatrix Intelligent Centralized Controller
The Aviatrix controller is the brain of the cloud network platform. The platform leverages the centralized intelligence and knowledge of the controller to dynamically program both native cloud network constructs as well as Aviatrix’s own gateway’s advanced services. Combined with Aviatrix’s Terraform integration, this design enables network and security Infrastructure-as- Code automation across a multi-cloud environment.
Aviatrix Gateways
Aviatrix Gateways deliver advanced cloud networking and security services. For this validated design Aviatrix Gateways are deployed to provide the distributed filtering services, based on policies FQDN (Fully Qualified Domain Names) Allow Lists or IP addresses to limit VPC or VNet egress traffic to known domain names or domain paths with wild card support. Aviatrix Gateways replace native cloud provider NAT (Network Address Translation) gateways and provide high throughput with limited compute requirements. Aviatrix Gateways are primarily deployed to deliver transit network and security services such as intelligent dynamic routing, active-active network high-availability, end-to-end and high-performance encryption and collect operational visibility data. Egress FQDN gateways can also operate as spoke gateways to deliver these services but may require higher-performance underlying cloud compute capacity.
Aviatrix CoPilot Visibility and Troubleshooting
Aviatrix CoPilot provides a global operational view of your multi-cloud network not available from AWS, Azure, or any other cloud provider. Enterprise IT teams – who need day-two operational visibility for cloud networking – use CoPilot’s dynamic topology mapping to maintain an accurate view of their global multi-cloud networks, FlowIQ to analyze global network traffic flows and global heat maps and time series trend charts to easily pinpoint and troubleshoot traffic anomalies. CoPilot leverages the intelligence and advanced network and security services delivered by the Aviatrix cloud network platform. With Aviatrix, cloud network and security operations teams have familiar day-two operational capabilities such as packet capture, trace route and ping to resolve problems faster. Operational features include resource tagging, resource clustering, infrastructure monitoring and alerting, all specifically built for multi-cloud network operations.
End-to-End and High-Performance Encryption
The Aviatrix Transit defaults to end-to-end encryption, however standard IPsec encryption is limited to 1.25 Gbps, so in active- active ECMP (Equal Cost Multi Path) high-availability mode provides 5Gbps bi-directional throughput. To achieve much higher IPsec encrypted throughput, Aviatrix’s high-performance encryption distributes processing across multiple cores and aggregates IPsec tunnels to reach wire speed encryption across public and private connections, such as AWS Direct Connect, Azure Express Route or internet (up to 90 Gbps).
Multi-Cloud Network Segmentation
Most enterprise corporate or regulatory security policies require network segmentation. It is either impossible to achieve network segmentation with native constructs or extremely difficult and tedious manual process that is prone to human error. Aviatrix designs deliver an automated solution that extends secure network segmentation beyond cloud boundaries, enabling multi-cloud security domains, with consistent, centrally managed, global network segmentation and connection policies.
Compliance
Many cloud workloads are subject to corporate or regulatory compliance, such as PCI (Payment Card Industry). Aviatrix FQDN filtering based egress security is an easy and quick to deploy solution to achieve compliance and audit requirements. The solution could also be integrated with 3rd-party audit and logging systems such as Splunk, Sumologic, Datadog and any other system that supports syslog and/or NetFlow.
Automation, Visibility and Operational Control
Deployment and updates easily fit into existing CI/CD pipelines with Terraform and the Aviatrix API (Application Programming Interfaces). Visibility and operational control over internet bound traffic is an essential element of any enterprise cloud architecture. Cloud applications with unrestricted access to the Internet-based services expose environment to attack. Best practices limit application network communications to only known Internet-based services. For example, app tier services that require build packages from GitHub must have access to github.com, but all other access should be filtered and blocked.
Design Considerations
When architecting multi-cloud network, SaaS organizations should consider secure self-service customer onboarding, availability, manageability, high-performance multi-cloud connectivity and cost to make sure proposed design meet the business and technical requirements.
Security
Workload level security i.e., SG/NSG/VMFW can help with the compliance but not sufficient on its own, defense in depth is the correct strategy. Aviatrix platform provides end-to-end high-performance encryption, stateful L4 firewalls and policy based Next Generation Firewall (NGFW) service insertion. This enables security controls to be centrally defined, automatically directing specified traffic to be routed for inspection, without complex manual route reconfigurations.
Repeatability
While customers onboarding, native features and their implementations may vary across CSP providers, leveraging the Aviatrix platform provides a repeatable framework for customer deployments, independent of cloud environment. SaaS resources can remain accessible to all end-customers regardless of how they were onboarded to the cloud without losing transit connectivity nor enterprise security.
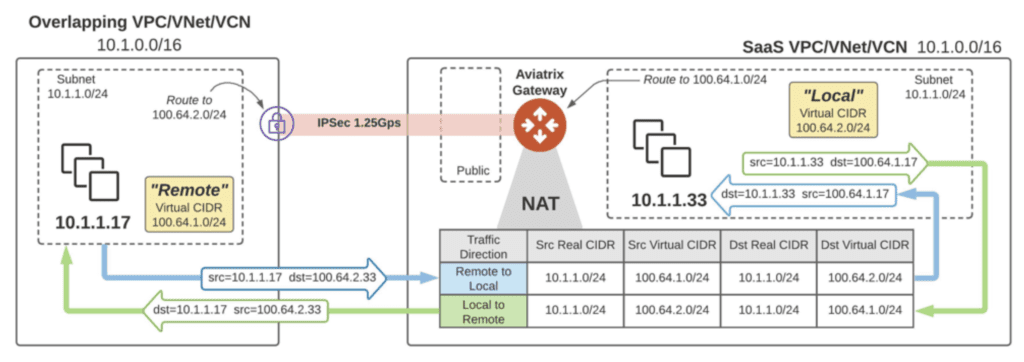
Custom Mapped-NAT Functionality (Overlapping IPs)
Complex overlapping IP addresses challenges can be easily solved by utilizing Aviatrix Custom Mapped-NAT feature. SaaS providers typically run into this challenge when connectivity customers to their shared services. If an organization runs out of private IP addresses, they can customize the NAT rules without burning unnecessary private IP addresses per end-customer.
Multi-Cloud Connectivity
Aviatrix controller builds logical tunnels between Aviatrix Gateways that reside in VPC/VNET/VCN and leveraging CoLo’s private backbone allows Aviatrix to provide a near line-rate encrypted transit data plane across multi-cloud environment. Aviatrix controller can leverage the Internet in the absence of a CoLo’s backbone and provide high performance, secure multi-cloud connectivity.
Private Link Traffic Inspection
Private Links helps SaaS Providers onboard their end- customers but leaves a big security hole since traffic inspection via NextGen Firewalls is either not possible or extremely difficult and manual to achieve. Aviatrix solves this challenge by its enterprise-class service insertion capability.
High-Availability
This validated design recommends at least two Aviatrix Gateways, each in different availability zones to provide infrastructure high availability. Gateways are deployed in Active/Active mode. In case of an outage, the Aviatrix Controller will automatically rebalance the load to the available gateway. The Aviatrix platform is constructed with redundant active/active gateways and leverages dynamic routing algorithms to ensure that resources remain accessible during failure scenarios. Additionally, full transit capabilities within and across clouds ensures that localized failures do not affect the overall connectivity to critical SaaS resources.
Operational Control
Simplified control and manageability is a crucial factor of this validated design. The Aviatrix cloud network platform allows several options including UI, API and Terraform.
Performance
Instance/VM size plays a key role in achieving desired performance goals, but performance is throttled by the Cloud Service Providers (CSP). It is important to determine the required transit throughput before implementing the solution to achieve optimal performance.
Cost Optimization
The Aviatrix multi-cloud network platform allows organizations to embrace a multi-cloud strategy without incurring the costs of lost productivity, project delays due to complexity, and extensive training sprawled across CSP’s for their individual and unique networking services. Some of the considerations are cost incurred due to network downtime, time-to-market in a new CSP, and Operational cost
Aviatrix Design
The Aviatrix cloud network platform is extremely flexible and can be deployed in many ways to meet business and technical requirements. Aviatrix is a low friction solution that fits easily in existing processes without requiring significant modifications to existing cloud provisioning workflows.
SaaS organizations can leverage Ali Cloud, AWS, Azure, GCP or OCI with the Aviatrix solution. The following validated design will focus on the architecture in and between AWS and Azure:
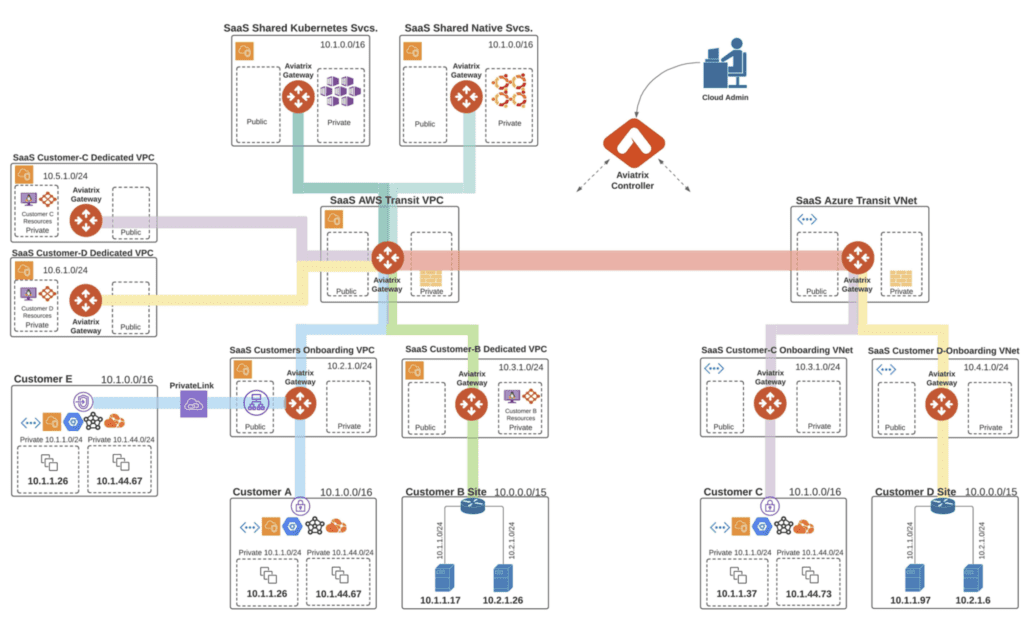
The above architecture provides flexibility onboarding customers to common VPC/VNet or a dedicated VPC/VNet per customer, where dedicated resources are hosted.
SaaS providers with the requirement for unidirectional traffic flow (from cloud to end-customer) also be use this architecture.
The design enables SaaS organizations to utilize the full capabilities of the Aviatrix cloud network platform to build and operate their cloud network, regardless of whether in a single cloud, single region, or multiple clouds across multiple regions. In a typical network design, the workloads are
spread across multiple cloud accounts and networks (VPCs/VNETs or VCNs – Virtual Cloud Networks) within a region. Aviatrix connects these networks in a transit architecture and builds consolidated edge connectivity to on-premises data centers and customer sites. At the core of the design is a global transit network built on Aviatrix Transit Gateways, which form the data plane. Each Spoke of the hub and spoke architecture is built on Aviatrix Spoke Gateways. Spoke Gateways are connected to Transit Gateways to form full mesh, high-performance, encrypted network connectivity between the spoke and the transit gateways. Hybrid, data-center connectivity is established by leveraging Border Gateway Protocol (BGP) or static connections. Overlapping IP challenges are solved with Aviatrix’s Customized NAT Mapped capabilities.
Visibility and Troubleshooting
This design provides a global operational view of the multi-cloud network including on-prem and cloud end-customers connections with latency monitors, active sessions and robust logging and alerting. With Aviatrix, cloud network and security operations teams have familiar day-two operational capabilities such as packet capture, trace route and ping to resolve problems faster.
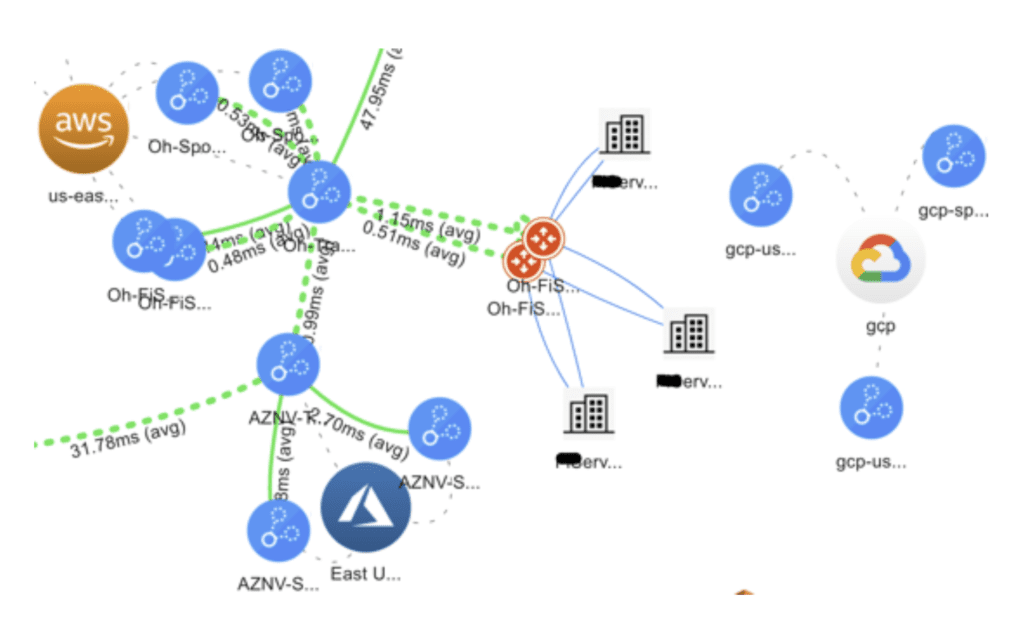
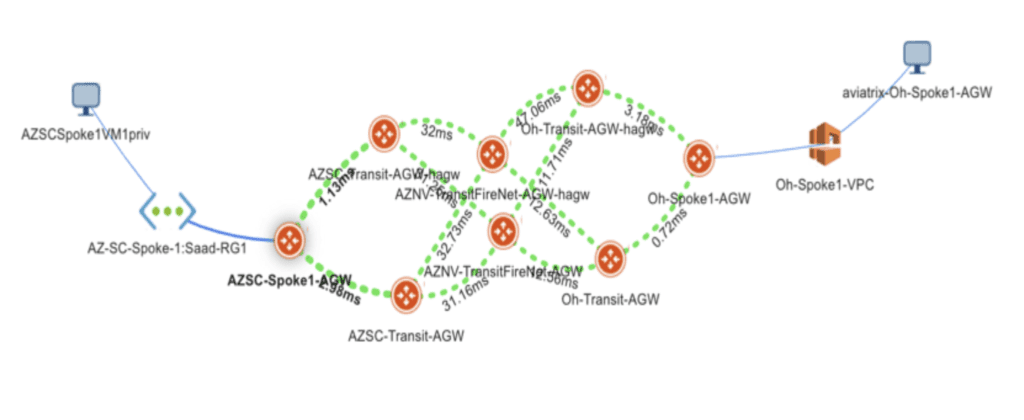
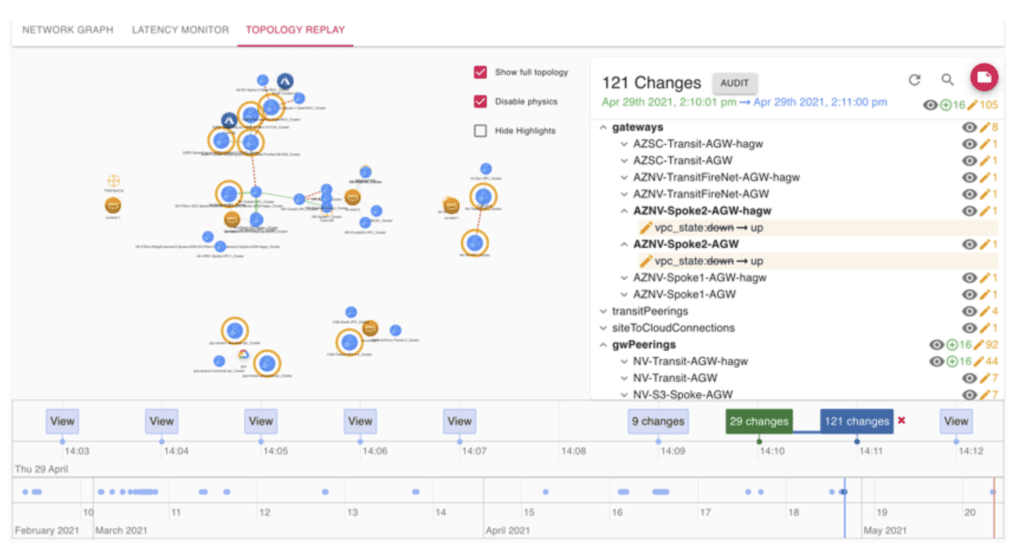
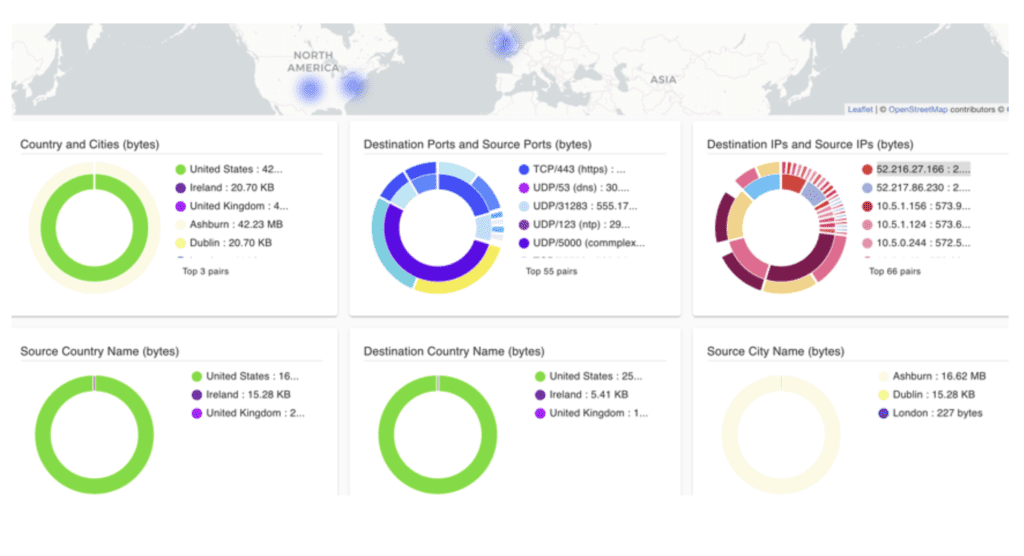
Design Benefits
- “Build vs Buy” decision becomes obvious as SaaS providers understands the Aviatrix MCNA capabilities and flexibility to solve extremely demanding use-cases
- Fast and secure customer onboarding (VPN provisioning) and cloud onboarding
- End-customers do not have to configure NAT on their IPsec enabled devices; Aviatrix controller seamlessly
provides that functionality on highly available Aviatrix Gateways - SaaS organizations easily provide end-to-end segmentation and segregation between end-customers by utilizing Aviatrix Multi-Cloud Network Segmentation feature which supports both cloud and on-prem end-customers
- Highly scalable architecture is capable of onboarding thousands of customers across multi-cloud environment
- SaaS organizations choose either private vs public inter-region or multi-cloud connectivity. Aviatrix platform
supports both options - This design is highly available; gateways are deployed in Active/Active mode with full mesh connectivity
- In this design, Aviatrix Gateway deployment is automated by the Aviatrix controller, which intelligently automates updates to VPC/VNET route tables and manages the lifecycle of entire interaction. This avoids common human errors and ensures network correctness
- The Aviatrix Controller automates redirection of traffic to NGFWs for inspection
- RBAC (Role-Based Access Control) for cloud network, security, operations engineers, and architects provide
added benefits - Global operational visibility is another important benefit that SaaS providers enjoys because no CSP provides visibility and troubleshooting tools because of black-box nature of their shared native constructs. In addition, SaaS providers have SLA obligations to their end customers that requires timely evidential data to uphold their business commitment
- SaaS providers easily support “law of the land” requirements based on customer and partner locations such as GDPR, Data residency and proof of operational resiliency
Information
Engage with Aviatrix
Online Documentation: docs.aviatrix.com
Help with MCNA Architecture or these validated designs: [email protected]
Join the Aviatrix Community
About the Author
Saad Mirza is a Principal Solutions Architect at Aviatrix with 20+ years of experience in networking and security. Saad has been solving enterprise’s complex challenges by providing guidance, architectural best practices and validated designs for hybrid and multi-cloud networks. These designs have been validated and adopted by Aviatrix enterprise customers.
Saad can be reached at [email protected]

