If you are looking for a solution to connect your users to the resources in Oracle Cloud (OCI), or to secure the internet-bound access from your OCI resources based on FQDNs, this article is for you.
Getting started with Aviatrix
Aviatrix is a powerful and advanced platform providing networking and security services in the public clouds, with multi-cloud optionality. While being comprehensive, it is also perfectly modular — you can start really small with just one or two services, and if you need to add more services, or expand into other clouds, you can do it at any time. The platform is flexible and can easily follow your current needs. Start anywhere, grow anywhere.
In this writeup I will focus on two services that our customers are deploying early on into their environments, while working out the bigger architecture with Aviatrix MCNA (Multi-Cloud Network Architecture). These services are UserVPN and FQDN Egress Filtering.
UserVPN
Let’s first talk about UserVPN. This topic can be very simple (“I want to give my remote users access to all the resources in OCI”), or very advanced (“I want to give my remote users access to specific resources in OCI and other clouds, based on their group assignment in my SAML Identity Provider, all sprinkled with MFA”), or anything in between. Regardless of what you need, Aviatrix has got your back.
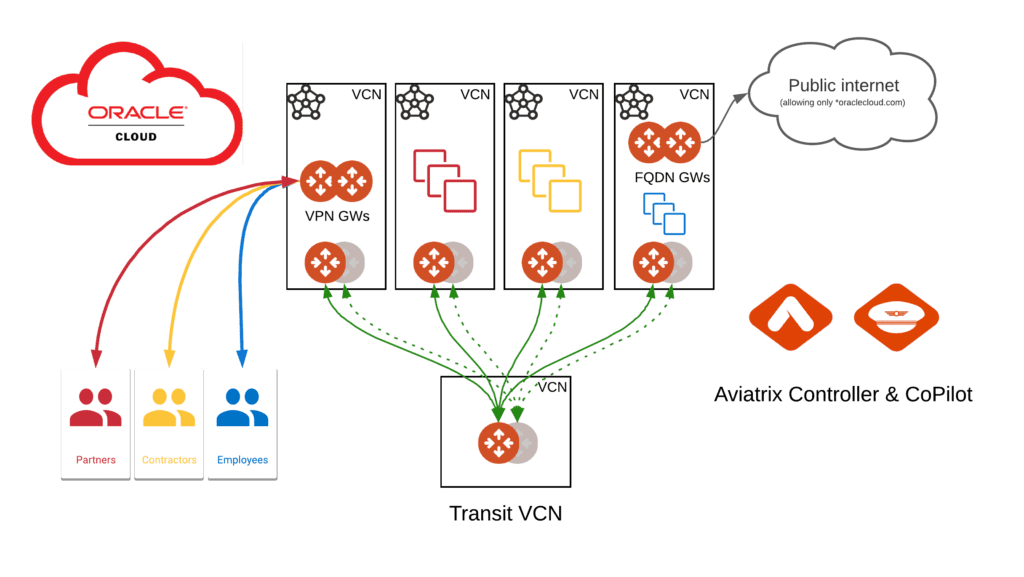
We can easily deploy a VPN service which will land your users in a dedicated VCN and from there they will be able to access the resources which you allow them to. User authentication and authorization can be handled directly by Aviatrix, or you can integrate Aviatrix with SAML Identity Provider.
In the diagram above there are 3 main group of users, accessing the OCI environment through the same VPN GWs, but each group is allowed granular access only to selected resources.
Configuration of the Aviatrix VPN service is detailed here: https://docs.aviatrix.com/HowTos/uservpn.html
Joint OCI-Aviatrix blog on UserVPN can be found here:
https://blogs.oracle.com/cloud-infrastructure/simple-secure-cloud-access-with-aviatrix-user-vpn
FQDN Egress Filtering
Now let’s take a look at the other topic — securing the outbound traffic from your private OCI resources to the public internet.
We see many customers want to provide additional level of security for their public internet connectivity, allowing only specific domains to be accessed. You may need your private VMs to fetch their latest code from GitHub, or download updates to the Ubuntu packages. But you don’t want to allow full outbound access.
You can try and use some native services which OCI offers — Security Lists or Network Security Groups. The challenge with them is that they work only on IP level, and not on the FQDN domain level. So first you’d need to find out what IPs to allow, then hardcode these IPs in your SL/NSG configuration, and keep on monitoring for IP changes.
Aviatrix offers a much simpler solution. With FQDN Filtering you specify a domain, optionally with a wildcard (e.g. *.ubuntu.com, *.github.com) and the allowed port/protocol for the outbound configuration.
Here’s a simple example of my OCI private VM trying to access two domains: google.com and oraclecloud.com. Only the latter is on the allowed list on the FQDN GW (see the diagram above).

