TLDR; MACSec exposes your data in the clear at every router hop along the way. IPSec provides better end-to-end security with high throughput with technology available from Aviatrix.
If your company has sensitive data to transmit over a network, you will want that data to be encrypted as much as possible and sent over a private connection. Regulatory compliance is a serious matter. It’s not enough to simply “trust” that application developers are always encrypting your data. You will need to enforce security for all traffic using network-based encryption, such as with IPSec or MACSec.
In this article you will learn why IPSec provides better end-to-end security than MACSec, with high performance throughput, using technology from Aviatrix.
What is MACSec?
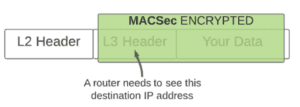
Cloud providers offer MACSec encryption as an option to secure sensitive traffic on private direct connections from your site to their cloud. MACSec stands for Media Access Control Security. The term “Media” means the physical cable that carries signals from one device to another. The name is appropriate because MACSec secures your data as it travels on the media (like fiber optic cables) that connect two network devices together, and only on the media. It does not protect your data as it travels through network equipment. The very first thing the receiving device needs to do is decrypt the MACSec encryption as it pulls your data off the media.
In a nutshell, MACSec protects your data as it travels on a cable between two routers, and only if it is enabled on both routers using that link. MACSec operates at Layer 2, which means it also encrypts essential Layer 3 information in your IP packet that a router needs to make a routing decision. This is why a router immediately decrypts MACSec traffic upon receiving it.
The one thing MACSec does very well is speed. MACSec is embedded in the silicon responsible for transmitting and receiving data on the media (sometimes called the PHY layer). It can operate as fast as the media is capable of, encrypting and decrypting data with no performance penalty. However, this speed comes at the cost of special hardware that a router must have to support MACSec.
A false sense of MACSec security
There is one fundamental problem with believing that MACSec will secure your sensitive traffic as it travels over a network. With MACSec alone, your sensitive data will be unencrypted and exposed as it travels through each router [1] along the path to its destination (e.g., somewhere in the cloud).
This is because MACSec encrypts the Layer 3 routing information contained in your IP packet, including the all-important destination IP address. When a router interface receives a MACSec encrypted frame, the very first thing it must do is decrypt the frame and all the data it contains. With your IP packet (and data) decrypted, the router can now look at the destination IP address to make a routing decision, and other decisions too like rate-limiting.
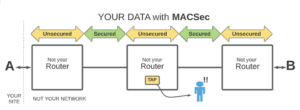
Your unencrypted data travels through the router towards a destination interface. Inside the router, your data is processed by a sophisticated network of silicon that allows the router to do many things — such as making a copy of your data to send somewhere else using a common feature called Port Mirroring, or SPAN [2]. Either intentionally or accidentally, someone can make a copy of your unencrypted data as it travels through the router, and you would never know about it. A router is the perfect place to TAP and snoop your data.
IPSec provides better end-to-end security.
IPSec on the other hand operates at Layer 3 and encrypts traffic between any two IPSec enabled endpoints that you own and control. IPSec encrypts your data and encapsulates it inside a new IP packet with the destination IP address unencrypted and readable by routers (the destination being the other IPSec endpoint).
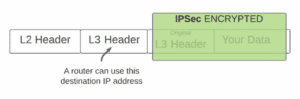
The outer IPSec encapsulation allows a router to do its job without decrypting your data. It can read the destination IP address of your IPSec packet and make routing decisions. Even if the router really wanted to decrypt your data it would be impossible, because only the IPSec endpoints have the keys to your encryption. Whereas with MACSec the router owns the keys to decrypt your data (because it needs to).
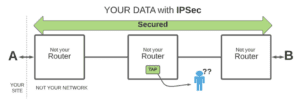
This means that with IPSec your data remains secure as it travels through routers that you do not own and control. If something happens inside one of those routers, like someone enabling a tap feature to send a copy of your data somewhere else [2], that data will be useless to whoever sees it.
How to get high performance with IPSec
While it is obvious that IPSec is better for securing your sensitive data, it does not have the same line-rate performance of MACSec. This is because IPSec is a CPU intensive process that runs on an x86 machine as a single-threaded process. Hence, IPSec will only perform as fast as that one CPU core can go, which is about 1.25 Gbps. To get better performance from IPSec you’ll need to have multiple endpoints running multiple tunnels in parallel across multiple CPU cores.
Aviatrix has built a patented technology that does exactly that and makes it easy for you to use. The Aviatrix controller creates multiple IPSec tunnels between two Aviatrix Gateways and aligns each tunnel to a unique CPU core on each machine. It’s called High Performance Encryption (HPE). And it gives you the full IPSec performance [3] that an x86 machine can really offer, by utilizing all its CPU cores.
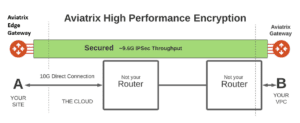
To keep your network architecture simple, Aviatrix HPE manages the IPSec tunnels in a single logical connection for you. The Aviatrix gateways will load balance traffic on the IPSec tunnels and react to any failures without any additional load balancing and routing protocols that complicate your network. You simply deploy one Aviatrix Edge Gateway at your on-premises location and another in your cloud environment and let the Aviatrix Controller build the IPSec connections for you. [4].
One Aviatrix Edge Gateway can support up to 10 Gbps of encrypted throughput. And once you have squeezed the most out of one, you can add another, creating an additional network path for redundancy and load balancing.
Important: You should know exactly how your data is being transmitted across the network, such as what kind of systems are sending data, how many of them, and how many total TCP flows will be in-flight at any given time. Aviatrix uses per-flow load balancing across the parallel IPSec tunnels, so if all data is being transferred with a single TCP flow from a single system (unlikely but possible), your application throughput will be limited to that of a single IPSec tunnel.
Without technology like this, your network architecture could get complicated. You would have to design multiple IPSec tunnels yourself across multiple devices in a fan-out topology and properly configure the routing, load balancing, and redundancy. And for someone who does not know about Aviatrix, this is what makes the less secure MACSec option appealing. They just want to keep the network topology simple, while encrypting with high performance.
Conclusion
MACSec provides line-rate performance but brings considerable risk because your data is unencrypted as it moves through network devices, where it is vulnerable to being tapped and observed, and copied without your knowledge. The best way to secure your data when connecting to the cloud is with IPSec, because your data remains protected through the entire path between IPSec endpoints. And you can use technology like Aviatrix high-performance encryption to get the throughput you need in a simplified topology. If you want to learn more and dive deeper, you can request a live demo here.
Did you know with MACSec, sensitive data travels through each router unencrypted? Wondering what other common challenges enterprises frequently encounter with cloud networking and security (and how to avoid them)? Download our Ebook and get practical steps for turning your cloud network into the business enabler it was always meant to be.
If you want to learn more and dive deeper, scan this QR code to get in touch:

References:
[1] “Layer 2-Layer 7 services can be performed on the Ethernet frame or IP Packet since it is “in the clear” prior to being encrypted on egress”: Innovations in Ethernet Encryption (802.1AE – MACsec) for Securing High Speed (1-100GE) WAN Deployments White Paper – Cisco
[2] “This sends a copy of the traffic to another port on the switch that has been connected to a SwitchProbe device, another Remote Monitoring (RMON) probe or security device”: How to configure port monitoring (SPAN) on a Catalyst 2940, 2950, 2955, 2970, 3550 or 3750 series sw… – Cisco Community
[3] HPE Insane Mode Encryption Performance — aviatrix_docs documentation
[4] Aviatrix Edge Design Patterns :: Documentation


